Synadia Platform
HTTP Gateway Architecture and Dependencies
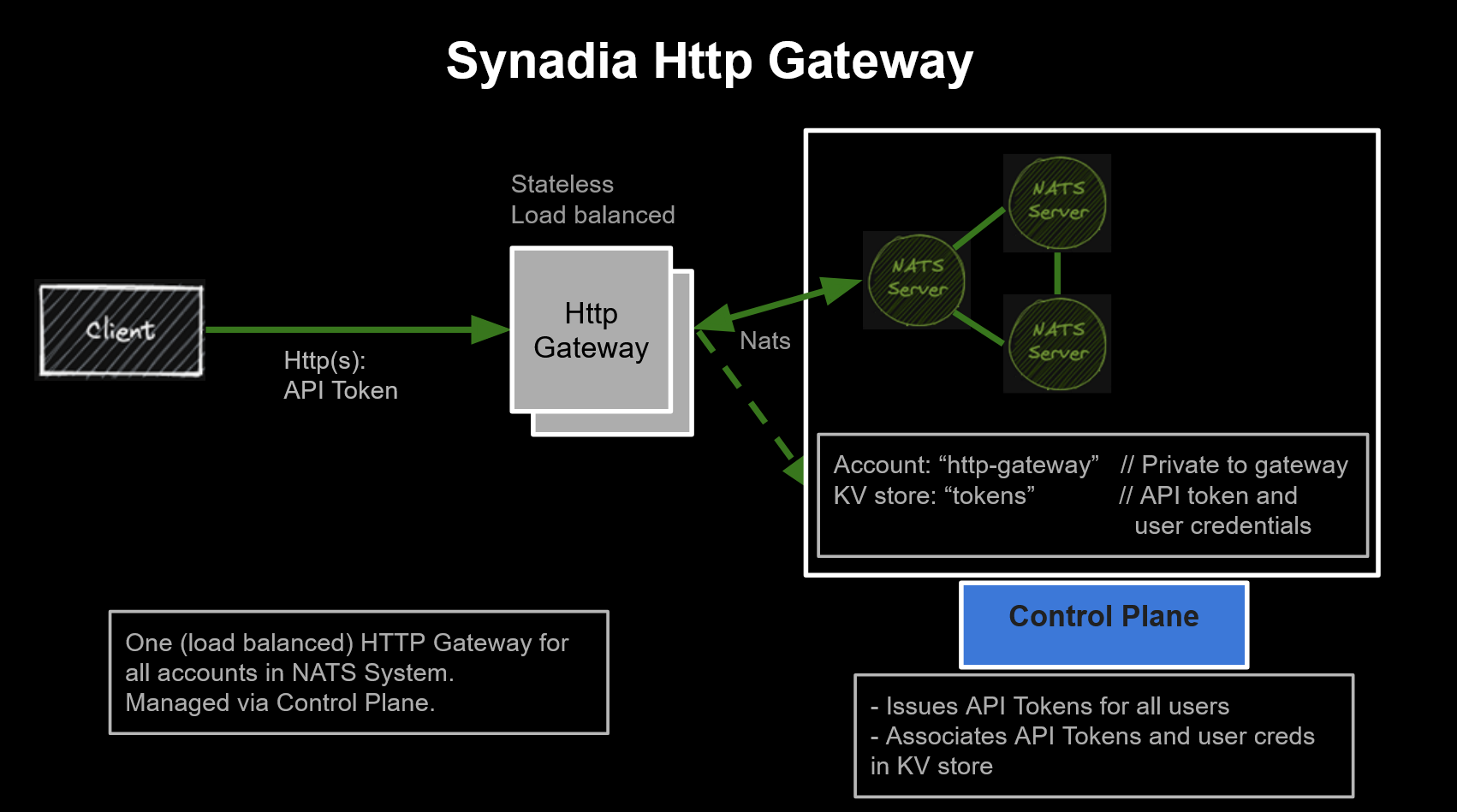
Components
HTTP Gateway
- Stateless Container
- Optionally multiple deployments, load balanced or geographically distributed
- Access via API Token
Pre-existing NATS system
- Managed by Control Plane
- One HTTP Gateway will access one NATS system.
- Access configured on a per user basis
HTTP-Gateway account and user
- Stores API tokens and gateway state in KV store
tokensin accounthttp-gateway - This Could be a shared account, but this is not recommended
- User
http-gateway
- Stores API tokens and gateway state in KV store
Control Plane
- Enables user access (any account) by creating API tokens and storing them (with associated user credentials) in the
tokensKV store.
- Enables user access (any account) by creating API tokens and storing them (with associated user credentials) in the
Security and Access Control
- The only configured credentials the API Gateway deployment requires are for accessing the
http-gatewayuser. - Credentials for accessing other users, for which API token have been issued, are retrieved at runtime from the
tokensKV store.
Notes
User management in the NATS System/Control Plane is not effected by the HTTP Gateway. User permissions are managed through Control Plane. API Tokens can be issued for pre-existing users. It is recommendable, but not required to create dedicated users for HTTP Gateway access
Control Plane does not manage the API Gateway directly. Any number of gateway deployments can connect to the http-gateway user.
Only one gateway account is supported today (all gateways have the same capabilities). Technically multiple configurations (in separate http-gateway accounts) could be maintained for multiple distinct HTTP Gateways. Control Plane does not (yet) support managing those.
